Table of contents:
Introduction
Recipes are a fundamental concept within the Bosch IoT Rollouts System Software Update (SOUP) extension. They serve as system update definitions and encompass crucial information, including:
- Identification of the targeted systems for the update
- Specification of the software to be installed on each module
- Definition of the desired target state of the system after the update has been applied
- Optional pre- and post-system update scripts
- Inclusion of user-related information within the recipe metadata
- Meta information such as the publishing date or tags associated with the recipe
Recipes play a central role in orchestrating and managing system updates, providing a comprehensive framework for ensuring efficient and effective software updates within the Bosch IoT Rollouts ecosystem.
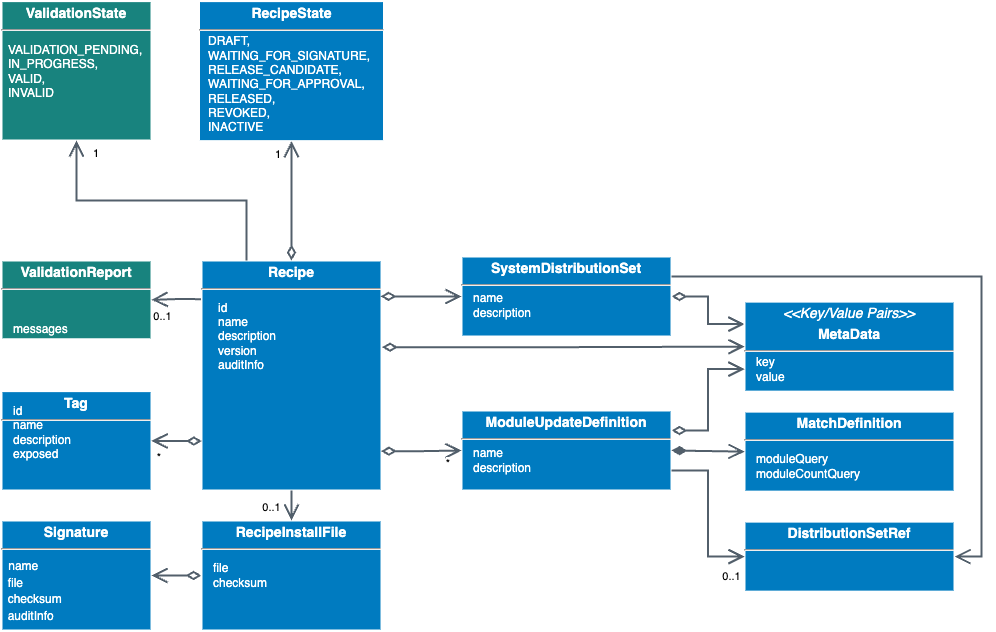
Recipe data model
A recipe is a system update definition, that specifies a set of matching modules, references distribution sets, and describes the desired system state after the recipe has been applied. Besides basic properties (name, version, and description of the recipe), the recipe has
- Audit information detailing creation, modification, publication, and approval
- Lifecycle status (refer to Recipe lifecycle)
- Validity status (refer to Recipe validation)
- Module update definitions for identifying matching system (refer to Module update definition), and references to software for module updates, if applicable
- System distribution sets for referencing non-module-related artifacts (e.g., system release notes, pre- or post-install scripts) (refer to System distribution set)
- Metadata for providing additional custom information (primarily used during transformation to the recipe file)
- Tags for efficient filtering within the backend or on the Install API
- The recipe file itself (refer to Recipe file)
Module update definition
A module update definition consists of a three elements:
- The module query (a.k.a. Module match) identifies a set of modules (based on properties from the controller attributes).
- The count specifies the expected number of matching modules within a system.
- The optional distribution set specifies the software that should be applied to the matching modules. If no distribution set is specified, the matching modules need to be present in the system but will not be updated.
Module match query syntax
The module match queries are similar to target filter queries, however, they only support a subset as given in the table below:
Operator | Description | Example |
|---|---|---|
| equals |
|
| not equals |
|
| less than |
|
| less then or equals |
|
| greater than or equals |
|
| greater than |
|
| equals one entry in the list |
|
| does not equal any entry in the list |
|
| logical and composition of two terms.
|
|
All attributes are strings. However, using string compare for versions does not make sense. Therefore, the following sorting is applied:
- natural sort order for properties configured in
soup.systemreport.version.property.names(SOUP Tenant configuration) - all other properties use string compare.
Module count query syntax
Operator | Description | Example | Explanation |
|---|---|---|---|
| equals | count==1 | Mandatory module that must be there exactly once in the system. |
| less than | count=lt=2 | Optional module that can be maximum once in the system. |
| less then or equals | count=le=2 | Optional module that can be maximum twice in the system. |
| greater than or equals | count=ge=0 | Optional module that can be part in any number within the system. |
| greater than | count=gt=0 | Mandatory module, that must be at least once in the system. |
System distribution set
A system distribution set specifies distribution sets that are required on system level (e.g. system release notes, install scripts).
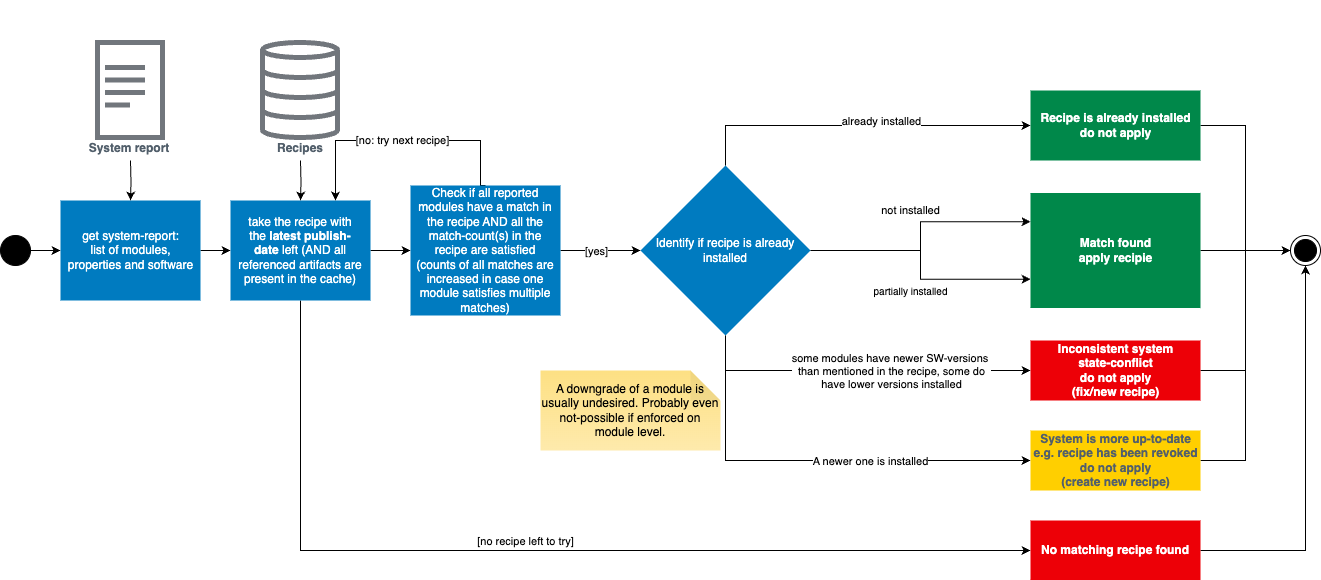
Recipe match algorithm
The recipe match algorithm describes how a matching recipe for a given system is identified. For a successful match, a recipe has a module update definition for every module within the system, satisfying both the match query and count requirements. In cases where multiple recipes could potentially match a system, the algorithm selects the most recent one based on its publish date. The algorithm is triggered automatically for
- all systems, if a recipe changed its status (i.e., on promote, demote, approve, revoke, deactivate),
- on a single system, if a system is updated (e.g. a new system report has been received).
After the recipe match job executed the algorithm, all systems have a matching recipe and/or matching release candidate recipe depending on the output of the job.
Recipe coverage
When a recipe is activated, it is crucial for the update coordinator to ascertain the number of systems that will be impacted by the recipe. This information is valuable in assessing both the extent of coverage and the potential consequences in case of any issues. After the execution of the recipe match, the coverage of the recipe is presented on a relative scale ranging from very low to very high, depending on the number of matching systems.
Icon | Name | Description |
|---|---|---|
Very high | The recipe matches more than 80% of the systems. | |
High | The recipe matches between 61% and 80% of the systems. | |
Medium | The recipe matches between 41% and 60% of the systems. | |
Low | The recipe matches between 21% and 40% of the systems. | |
Very low | The recipe matches less than 20% of the systems. | |
No matches were found | No system matches the given recipe. | |
In progress | The coverage calculation is in progress. |
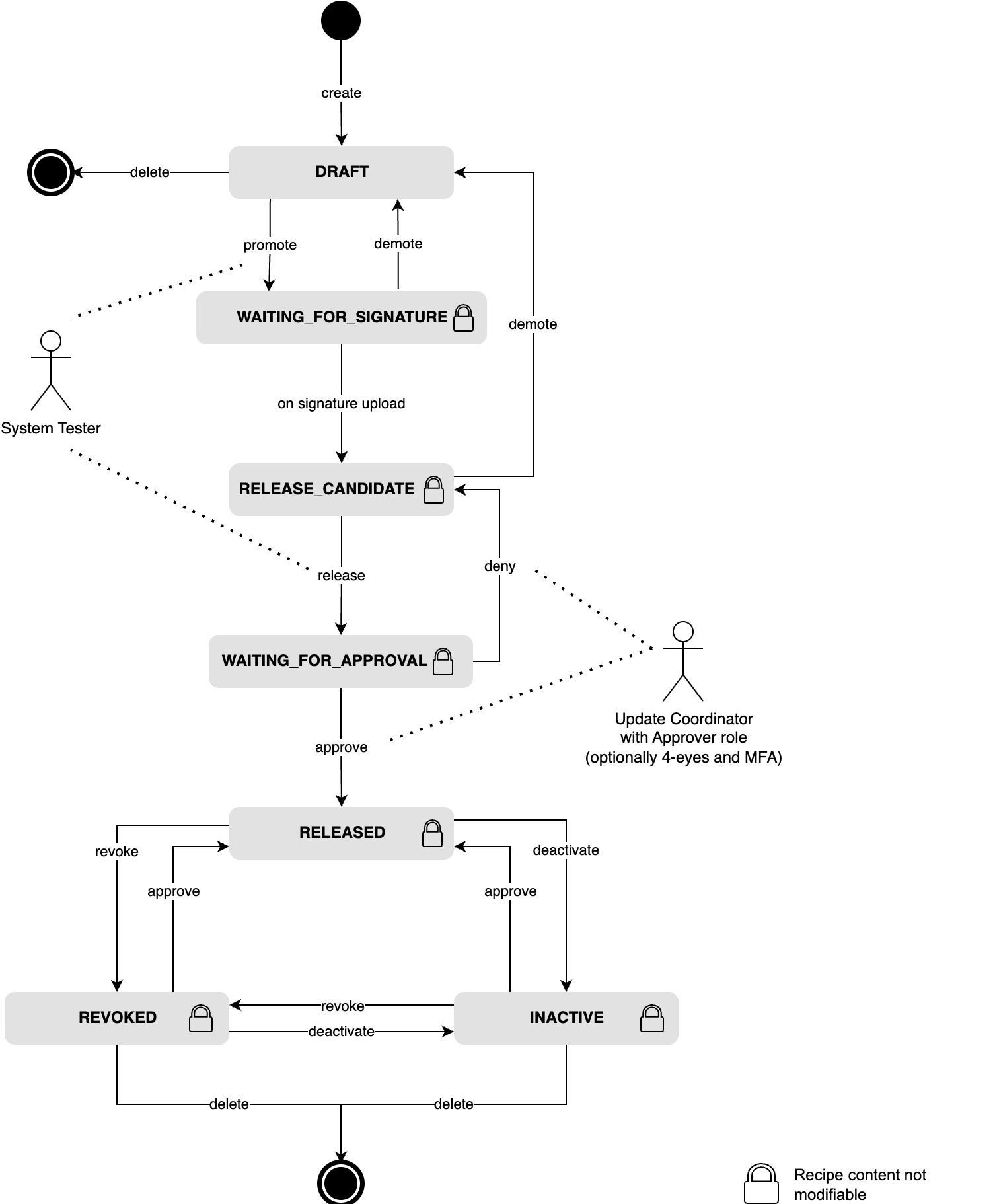
Recipe lifecycle
The lifecycle of a recipe can be controlled via the Recipe UI or Management API. Lifecycle management enables System responsibles to
- release a recipe for testing,
- release and approve a recipe for productive system updates,
- take a recipe offline which is suspected to cause issues in the field, or
- retire a recipe which is no longer needed (because of newer recipe versions).
Defined recipe states
Icon | State | Description | Exposed on Install API | Modifiable | Deletable |
|---|---|---|---|---|---|
DRAFT | Initial state right after creating (or uploading) the recipe. | No | Yes | Yes | |
WAITING_FOR_SIGNATURE | Recipe file is created and the signature needs to be uploaded. Recipe must be valid to switch into that state | No | No* | No | |
RELEASE_CANDIDATE | Recipe is ready for verification testing. | Yes - scope testing | No* | No | |
WAITING_FOR_APPROVAL | Recipe has passed all verification tests and can be released once it has been approved by an approver. | Yes - scope testing | No* | No | |
RELEASED | Recipe is released and can be applied to productive systems. | Yes - scope production | No* | No | |
INACTIVE | A released recipe which has been deactivated may still be used for system updates. For example, a newer version of the recipe is available. | Yes - scope production | No* | Yes | |
REVOKED | A released recipe which has been revoked must not be used for system updates. For example, the recipe needs to be verified due to a potential error/bug. | Yes - scope production | No* | Yes |
*) Recipe content is read-only, but tags can still be modified.
Recipe state transitions
The following picture illustrates the lifecycle of a recipe. The state transition actions are typically triggered by a system responsible or update coordinator who is authorized to do so.
Explanatory notes:
- When a recipe is promoted to RELEASE_CANDIDATE, it becomes accessible via the Install API. Draft recipes, on the other hand, are only accessible through the Management API.
- Uploading a signature during the WAITING_FOR_SIGNATURE state automatically moves the recipe to the RELEASE_CANDIDATE state.
- The release action is used to initiate the release of the recipe, triggering a request for final approval.
- The approval action, which is used to push a recipe into RELEASED state, requires a special permission.
- Once a recipe is in the REVOKED or INACTIVE state, it must be re-approved to be put back into the RELEASED state.
- Deletion of recipes, applicable only for recipes in the DRAFT, REVOKED, or INACTIVE state, requires special permission.
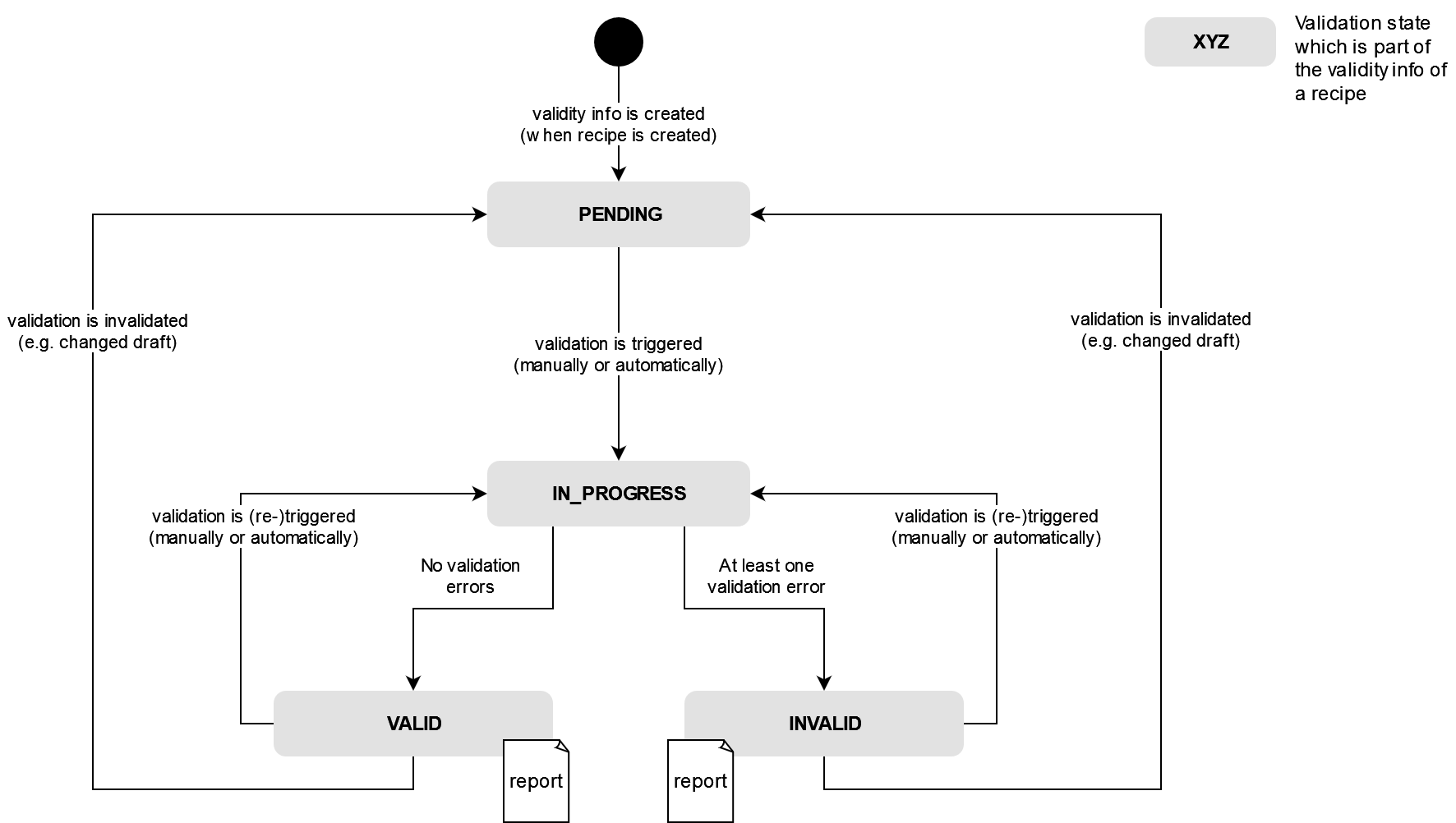
Recipe validation
Recipe validation is a crucial step in ensuring the integrity and reliability of recipes before they are exposed to the systems through the Install API. Its primary purpose is to verify that the management representation of a recipe can be successfully transformed into a valid install representation, also known as the recipe file. By undergoing the validation process, recipes are thoroughly examined to identify any potential faults or errors. This validation is a prerequisite for promoting a recipe from the DRAFT stage, as only valid recipes can proceed further in the lifecycle. Through recipe validation, SOUP guarantees that only syntactically correct and complete recipes are made available for system updates, enhancing the overall stability and reliability of the update process.
Available validations
Following is a list of available recipe validations and whether they are generic or can be configured for each tenant.
Validation | Default | Scope | Severity | Description |
|---|---|---|---|---|
Distribution set | Yes | Tenant | Error | The distribution set validation checks, if the referenced distribution sets
|
Match query | Yes | Tenant | Error | The match query validation checks that the provided module query is syntactically correct (e.g. only supported operators are used). |
Metadata | No | Recipe type | Error | The metadata validator allows you to specify optional and mandatory metadata keys, as well as a regular expression (RegEx) to validate the metadata values of metadata. If configured, only the specified keys are allowed; otherwise, arbitrary metadata keys and values are permitted. |
Total artifact size | No | Recipe type | Warning and error | The total artifact size validator allows the configuration of a maximum total artifact size for a recipe. In addition, a list of software module types can be provided, which will be excluded from the calculation (e.g., release notes). |
Distribution set assignment | No | Recipe type | Error | The distribution set assignment validator ensures that all module update definitions of an updatable module type have a distribution set assigned. Updatable module types that should not be updated with recipes of this recipe type need to be added to the exclusion list. Additionally, it verifies that there is at least one distribution set for each compatible distribution set type associated with the system type. |
Tag assignment | No | Recipe type | Error | The tag assignment validator allows you to require recipes to have certain tags by defining a regular expression (RegEx) for matching their name and specifying whether they should be exposed or not. The validator checks if the recipe has at least one matching tag for every rule. It is possible that one tag can satisfy multiple rules. |
Validity states
Icon | State | Description |
|---|---|---|
PENDING | There is currently no validation result available. It is either a new recipe, or was changed since the last validation. | |
IN_PROGRESS | The validation is ongoing. | |
VALID | The recipe has successfully passed the validation. If the recipe is in DRAFT state it can be promoted now. | |
INVALID | There are validation errors. Please check the validation result. After the errors have been rectified, a re-validation can be triggered. |
Validity state machine