By rolling out updates to devices, companies cannot only mend software issues quickly. More and more manufacturers also understand software updates as a means to prolong a product’s life cycle by adding new features. This in turn can form the basis for implementing completely new business models.
Providing software updates over the air (SOTA) makes the whole process more convenient and efficient. However, this does not mean that SOTA is a simple undertaking from the manufacturer’s perspective. There are many steps to consider, such as assigning updates to eligible devices, carefully managing large-scale software rollouts, and continuously monitoring update processes. One topic is particularly important – security.
Security during the artifact life cycle
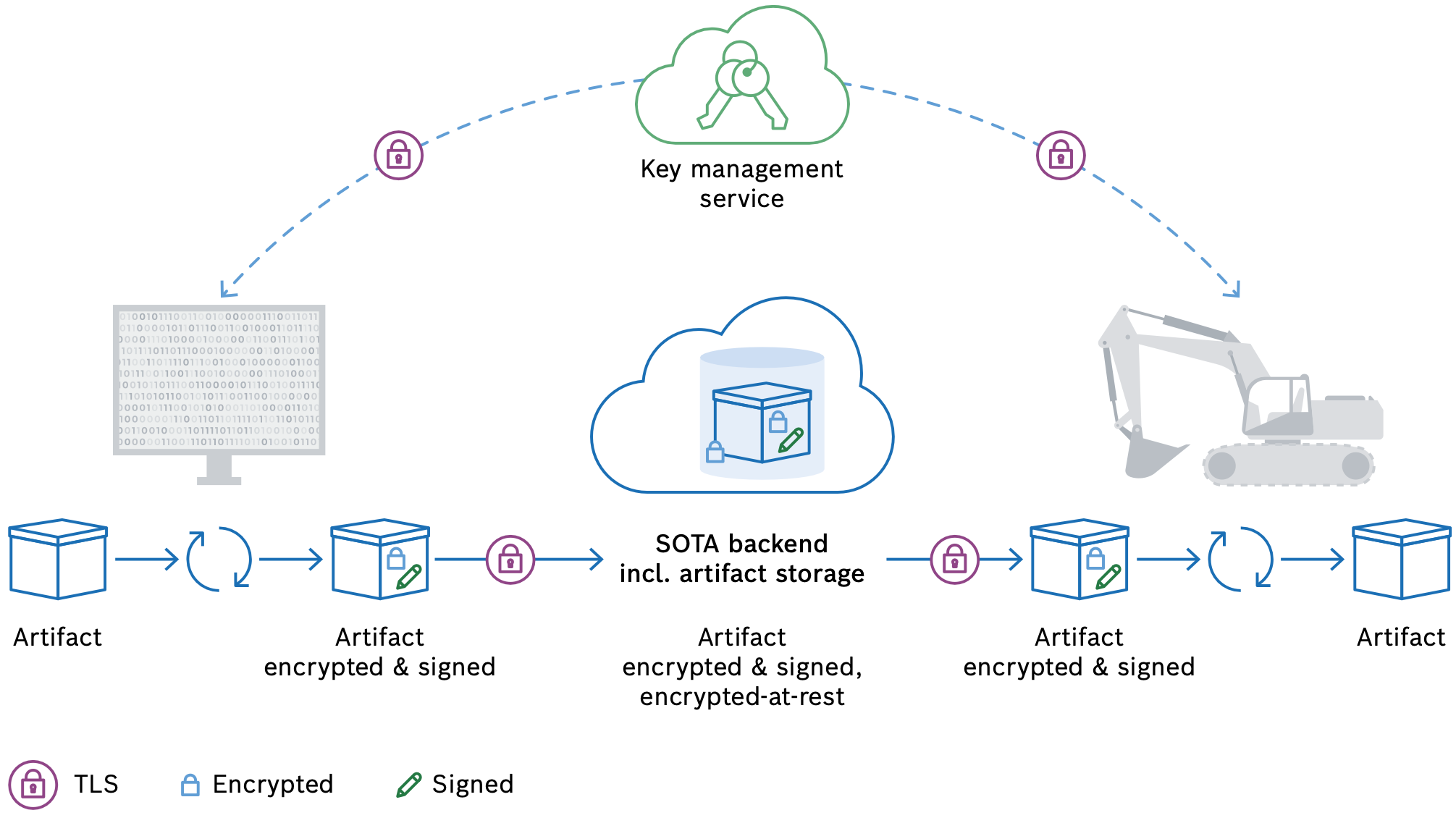
There are various ways in which a software artifact can be corrupted or compromised, be it technical issues during a file transfer or the interference of a malicious attacker. Companies have to find ways to safeguard the artifacts they provide over the air and ensure their confidentiality, authenticity, and integrity throughout their life cycle, starting with the software artifact’s development all the way to its deployment on a device. To achieve this, a trusted relationship has to be established between the authority that publishes the artifacts and the devices. This is where encryption and digital signatures come into play. These ensure end-to-end security, no matter if an artifact is in transit or at rest.
Encryption is used to guarantee communication confidentiality and ensures that the messages exchanged can only be read by the sender and the intended recipient – and not by third parties. Most commonly, communication between devices and the backend application is encrypted using an asymmetric encryption scheme. This approach involves a public key to encrypt messages and a private key to decrypt them. Granted, using symmetric encryption with generally shorter encryption keys makes the whole process quicker, less resource-consuming and more straightforward. Nevertheless, this approach is more vulnerable to security risks due to the nature of keeping the shared key as a secret on both ends of the communication – in particular, this applies to devices that an attacker can physically access to extract the secret.
Looking at the devices, a digital signature helps to verify the integrity of the artifacts they receive. For this, encryption principles as described above are applied to validate the signature. After successful validation, the package’s content can be accessed by applying the decryption procedure. Especially in large-scale software rollouts, software artifacts do not travel directly from a developer to the device, but are buffered in an artifact storage. To protect artifacts at rest in the backend, the persistence also has to be encrypted to prevent illicit access. In addition, the upload to and the download from the storage must be secured. This is where standard mechanisms such as transport layer security (TLS) come into play to ensure in-transit security.
The Sign & Encrypt extension helps projects to implement artifact encryption and signing, securing the artifact during its life cycle.